xxx
In June 2017, the National Institute of Standards and Technology revised its digital identity implementation guidelines in Special Publication 800-63. By the end of June 2018, all federal agencies will be required to have legacy systems and applications in compliance with the guidelines.
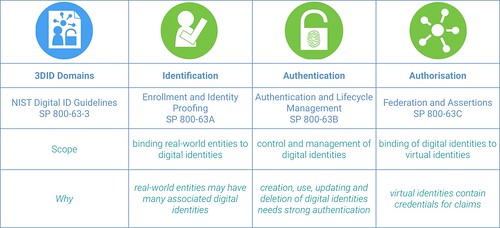
The NIST Digital Identity Guidelines use a three part model to create a standardised framework for dealing with the digital identity.
The NIST guidelines break up digital identity management into three sections: enrollment and identity proofing, authentication and life cycle management and .
If that breakdown sounds familiar to blog readers, it’s because it is congruent with the “Three Domain Identity” (3DID) model that we developed a few years ago to help our clients to formulate strategies around digital identity. Just as a reminder, the three domains in our model are “identification” (NIST’s enrollment, identity proofing), “authentication” (NIST’s authentication and life cycle management), and “authorisation” (NIST’s federation and assertions). I made a handy “cut out n’ keep” graphic.
xxx
So, it seems to me that the 3DID model provides an excellent basis for government and business to establish a shared digital identity paradigm.
Comments
Post a Comment